Maybe this is stating the obvious, but since I recently had a discussion with a peer regarding the stress of shipping firewalls and routers to remote sites where there wasn’t any OOB (Out Of Band) access for those times when you lock yourself out when you are, for instance, configuring routing across an IPSec tunnel and happen to destroy your default route. Not that this has ever happened to me.
To make sure that the device (running OPNSense) comes up without issue, at least on the WAN side of things, I need to simulate the Ethernet connection from the carrier-provided device. In this case, a Comcast Business (:vomit:) connection with a routed IP block.
To simulate the WAN connection we’ll need to setup a device with two Ethernet ports, running Linux (or another *nix or BSD, the concepts are very similar). I’m running Debian Bookworm on an SuperMicro C2758 in my lab that will serve as the upstream gateway and I have named it upstreamcc for this demo.
CCBI has assigned us a /30 block (50.100.110.160/30), which contains four (4) IP addresses, two (2) are usable.
| Network | First Usable host | Last Usable host | Broadcast |
| 50.100.110.160 | 50.100.110.161 | 50.100.110.162 | 50.100.110.163 |
Our setup looks something like this:
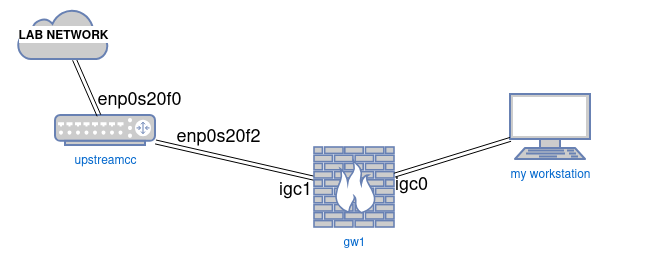
On upstreamcc, as root, we assign the gateway IP address that CCBI has given us, in this case our upstream gateway is 50.100.110.162 on interface enp0s20f2. We also want to enable ip forwarding as well because upstreamcc will be acting as a router.
root@upstreamcc:/home/hco# echo 1 > /proc/sys/net/ipv4/ip_forward
root@upstreamcc:/home/hco# ip link set dev enp0s20f2 up
root@upstreamcc:/home/hco# ip address add 50.100.110.162/30 dev enp0s20f2We should check to make sure our interface has been configured and is up
root@upstreamcc:/home/hco# ip a
...
2: enp0s20f0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 0c:c3:7a:68:a2:09 brd ff:ff:ff:ff:ff:ff
inet 192.168.XXX.XXX/24 brd 192.168.XXX.255 scope global dynamic enp0s20f0
valid_lft 32434sec preferred_lft 32434sec
inet6 fe80::ec4:7aff:fe68:f209/64 scope link
valid_lft forever preferred_lft forever
...
4: enp0s20f2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 0c:c4:7a:68:a2:12 brd ff:ff:ff:ff:ff:ff
inet 50.100.110.162/30 scope global enp0s20f2
valid_lft forever preferred_lft forever
inet6 fe80::ec4:7aff:fe68:a212/64 scope link
valid_lft forever preferred_lft forever
...
root@upstreamcc:/home/hco# Everything looks to be in place. Now we need to enable NAT on upstreamcc which will allow us to access the internet. On upstreamcc as root we enable masquerading between interfaces (really networks, but I digress)
root@upstreamcc:/home/hco# /sbin/iptables -t nat -A POSTROUTING -o enp0s20f0 -j MASQUERADEWe now need to permit traffic which we have allowed out of our firewall to be accepted back into our firewall.
root@upstreamcc:/home/hco# /sbin/iptables -A FORWARD -i enp0s20f0 -o enp0s20f2 -m state --state RELATED,ESTABLISHED -j ACCEPTFinally, we permit all traffic to pass on our “internal” interface
root@upstreamcc:/home/hco# /sbin/iptables -A FORWARD -i enp0s20f2 -o enp0s20f0 -j ACCEPTAt this point, we should be able to ping the WAN interface IP of the firewall (gw1) as well as the upstream gateway 50.100.110.162 from our workstation.
If we perform a traceroute from our connected workstation, we should clearly see our WAN gw1 gateway IP (50.100.110.162, hop 2) listed in the output. Hop 3 is my internet router and Hop 4
hco@workstation:~$ traceroute -n 8.8.8.8
1 10.XXX.XXX.XXX 0.295 ms 0.262 ms 0.397 ms
2 50.100.110.162 0.471 ms 0.376 ms 0.387 ms
3 192.168.XXX.XXX 3.784 ms 3.768 ms 3.747 ms
4 63.XXX.XXX.XXX 8.192 ms 8.882 ms 8.866 ms
5 70.XXX.XXX.XXX 8.126 ms 8.110 ms 8.095 ms
6 70.XXX.XXX.XXX 8.097 ms 8.739 ms 8.721 ms
7 70.XXX.XXX.XXX 13.675 ms 13.630 ms 13.536 ms
8 72.XXX.XXX.XXX 13.874 ms 11.626 ms 11.246 ms
9 8.8.8.8 13.839 ms 14.294 ms 14.258 ms
hco@workstation:~$There you go.
What’s that you say? 6 commands? Naw dog, two of those are configuring your local network interface, those don’t count.